


I spent weeks testing popular shadow IT detection tools to figure out which ones actually work. Here are the 7 shadow IT tools that proved themselves.
What is shadow IT, and why does it still exist?
Shadow IT is any tech your employees use without IT approval, usually because official processes feel too slow. It’s rarely malicious. But it creates a parallel tech stack that your security team can't see, can't control, and definitely can't protect.
The three main causes of shadow IT are:
- Speed beats bureaucracy: A 30-second signup beats a 3-week procurement cycle.
- Feature gaps: Approved tools lack specific features, so departments find alternatives.
- Budget constraints: When IT budgets are tight, departments use personal cards or expense reports to buy tools directly.
The result? You've got sensitive data scattered across dozens of apps you don't know exist. Good luck explaining that to your auditor.
The solution to this is a 2-part approach:
- Discovery answers "What exists?" It's about finding unauthorized apps, tracking spending, and mapping usage across your organization. Think of it as taking inventory.
- Management answers, "What do we do about it?" This is where you decide what stays, what goes, and what gets replaced.
Shadow IT vs. shadow AI
Shadow AI is a riskier evolution of the familiar shadow IT problem. It’s what happens when employees start using AI tools like ChatGPT or Copilot without IT oversight.
The motivation is the same. Employees want to be more productive, but the risks are harder to trace.
Traditional shadow IT meant your data might sit in an insecure app. With shadow AI, your AI models process your data and might leak it to competitors or hallucinate complete nonsense that influences real business decisions.
To make it even clearer, here's a quick side-by-side comparison:
Shadow IT in practice
The most frequent shadow IT patterns I see fall into these major categories:
- Department-level use of SaaS duplication. For example, one team uses Notion even though the company is supposed to use Asana.
- Unapproved communication tools like Slack plug-ins, WhatsApp groups for work, and Discord channels.
- A team licenses a tool like a BI add-on without asking for a security review.
These seemingly harmless shortcuts lead directly to predictable security risks down the line. Think about it:
- You've got sensitive company data floating around in apps that might not be secure or compliant with regulations. That's a data breach waiting to happen.
- You end up with wasted licenses. You might have five different teams all paying for separate project management tools.
- When a regulator asks us where our customer data is stored, you can't give them an accurate answer because it's scattered across a dozen unmanaged apps.
There are also hidden costs to these risks. You can't negotiate good deals with vendors if we don't know what people are buying, and can't support tools you don't know exist.
Shadow AI in practice
The MIT NANDA’s State of AI in Business 2026 found that employees in over 90% of companies regularly use personal AI tools for work. It's not just a few people here and there. It's basically everyone.
Shadow AI shows up as:
- Employees feeding sensitive documents or customer data into personal ChatGPT, Claude, Gemini, and other AI assistants.
- Unapproved AI copilots and extensions inside IDEs, Google Docs, or Excel that autocomplete or transform internal data.
- Internal AI automations or agents built by devs without security review.
The risks are harder to trace. You’ll be dealing with:
- Data leakage happening through training, not just storage. Your confidential info could pop up in another company's AI response.
- Hallucinations influencing decisions. AI might give you completely wrong information, and you might base your strategy on it.
- Audit trails not existing. When things go sideways, you can't trace what data went where or what the AI actually said.
Some of the hidden costs you should be aware of are engineers racking up huge API bills, or worse, the company losing its IP.
Why shadow IT and shadow AI need unified governance
Shadow IT and shadow AI need a single, unified governance strategy because they spring from the same root cause and create overlapping risks.
Both happen when teams get tired of waiting for the official, slow-moving process and go find a tool to get their job done.
But the line between them is disappearing. A sanctioned app (not Shadow IT) might have AI features that employees start using without approval (which is Shadow AI). If you're only looking for unapproved apps, you'll completely miss the AI risks happening inside the ones you've already approved.
Unified governance gives you one complete view of all the apps, APIs, and AI models your team is using. Once you have that visibility, you can revoke access, do security reviews, or provide better alternatives.
7 best shadow IT tools for 2026 (Overview)
Each tool solves part of the discovery and governance puzzle. You'll likely need a combination approach.
Here’s what the 7 tools we’ll discuss below are best for:
1. Superblocks
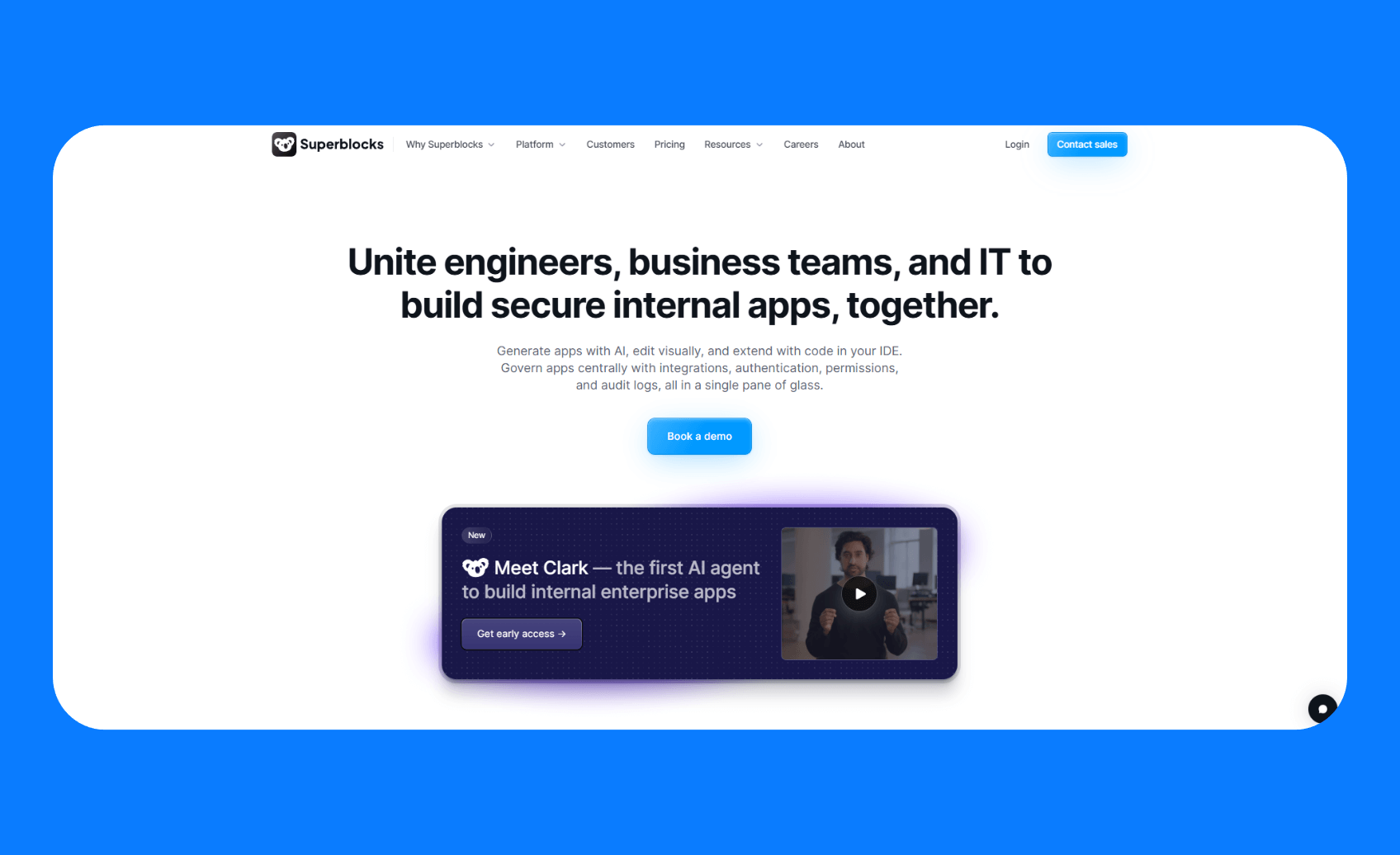
What it does: Superblocks reduces shadow IT by providing an AI app development platform where developers and business teams can build the internal tools they need, but within a centrally governed environment.
Who it’s for: CIOs, platform teams, security, or any org that wants to standardize their internal tooling ecosystem in one governed environment.
Key features
- Clark AI builds apps that automatically follow your security policies, coding best practices, and design systems.
- Centralized governance with SSO integration, RBAC, audit logs, secret management, and more.
- Hybrid deployment keeps sensitive data on-premises.
- Forward-deployed engineers provide on-site or virtual implementation help.
- Extensive integrations with almost any API or database, with 60+ native integrations and the option to build your own.
Pros
- It addresses the root cause of shadow IT by giving teams a fast-approved alternative.
- Every app built automatically adheres to security standards.
- It replaces multiple unauthorized tools with one governed platform.
Cons
- It won’t discover the shadow IT tools that employees are already using.
Pricing
Custom pricing based on the number of creators, end users, and whether you deploy fully in the cloud or use the on-prem agent.
Bottom line
If you're tired of playing whack-a-mole with unauthorized apps, Superblocks addresses the root cause. Your teams get the speed they want, you get the control you need.
2. Zluri
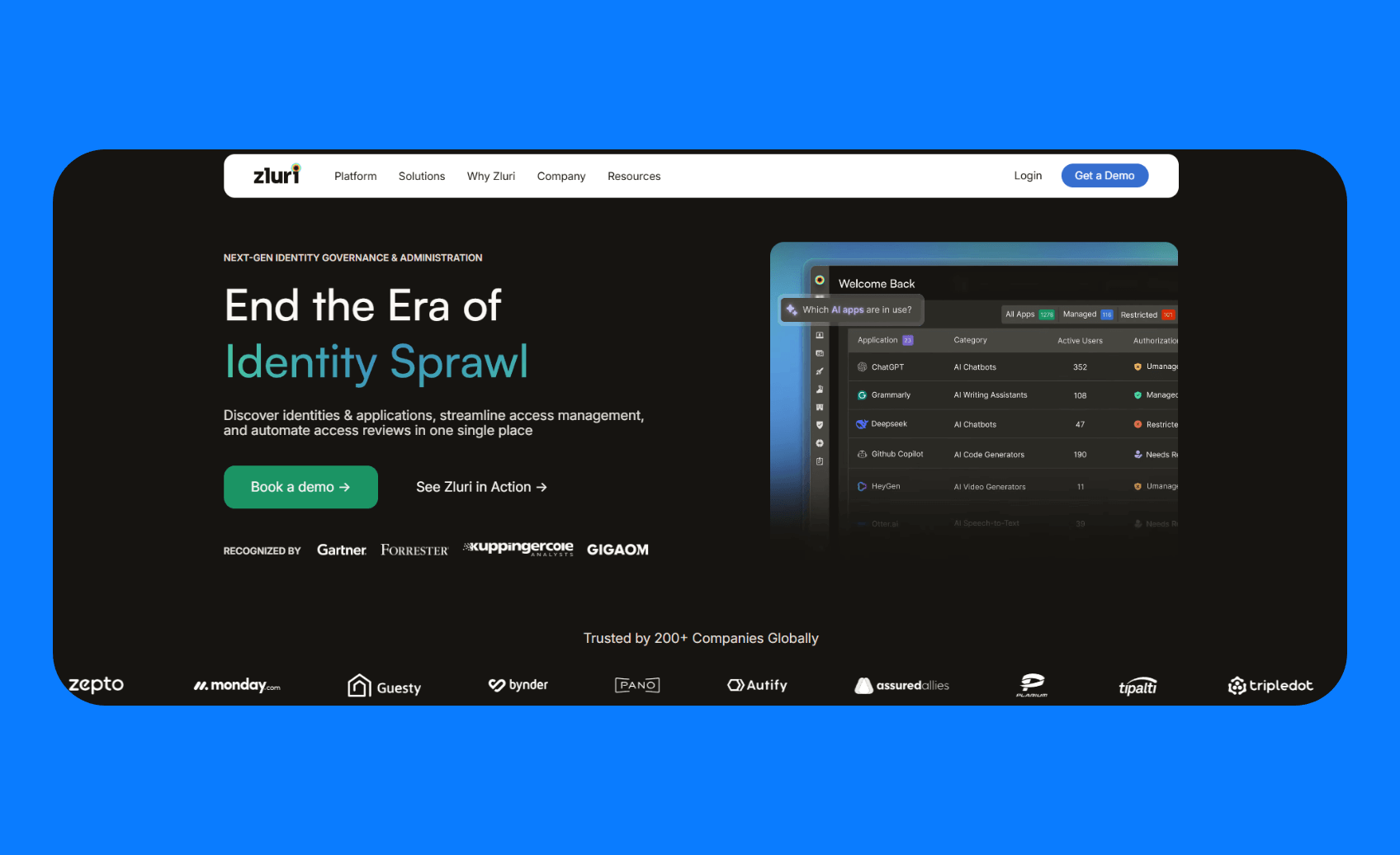
What it does: Zluri uses multiple discovery methods to identify SaaS apps. It integrates with SSO/IDP systems, finance and expense management software, direct API connections, and optional desktop agents and browser extensions.
Who it's for: IT directors who've been burned by "comprehensive" tools that missed half their apps and need bulletproof discovery.
Key features
- Multiple discovery methods, including SSO/IDP systems, finance integrations, and browser extensions.
- Automated risk scoring based on their security and compliance posture (e.g., SOC 2, ISO, HIPAA).
- Cost optimization that identifies duplicate subscriptions and unused licenses.
- Automated workflows for onboarding and offboarding employees.
Pros
- Multi-vector approach finds applications that other tools miss.
- Automation reduces manual onboarding and offboarding.
- It has 300 pre-built connectors that integrate with your existing identity, finance, and HR systems.
Cons
- Interface can feel overwhelming for smaller organizations.
- It occasionally generates false positives that trigger unnecessary alerts.
Pricing overview
Custom pricing. Contact their sales team for a quote.
Bottom line
When your top priority is to find every single application in your environment and then automate its management, Zluri is a top-tier choice.
3. Josys
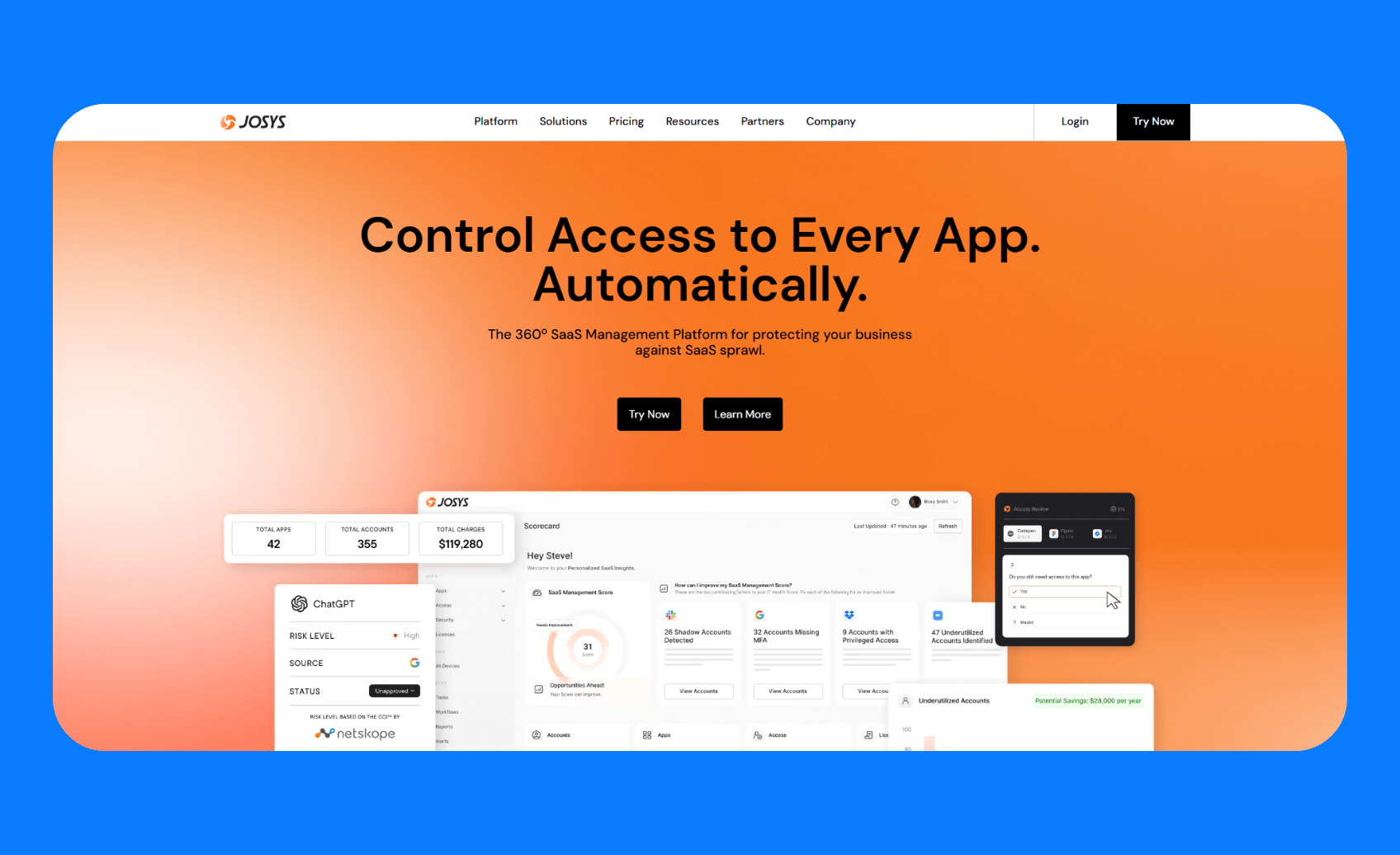
What it does: Josys is a unified SaaS and device management platform with a strong focus on discovering and governing shadow AI.
Who it's for: Security and IT teams that need a single platform to manage the entire lifecycle of both software and company devices.
Key features
- Shadow AI detection for ChatGPT, Claude, Midjourney, and other AI tools.
- Self-service employee portal with fast-track approval workflows that make it easy for employees to request tools.
- Automates user onboarding and offboarding for granting and revoking user access.
- Centralized dashboard for software and all corporate devices, like laptops and phones.
Pros
- It can catch AI tool usage patterns that introduce unique data leakage risks that traditional SaaS doesn’t.
- Integrating device management with SaaS management provides a combined view of your IT environment and risk surface.
- It surfaces unused SaaS licenses.
Cons
- It has limited integration options compared to larger competitors.
- Some niche applications aren't recognized in their database.
- Pricing transparency could be significantly better.
Pricing overview
You can get a free report of your organization's shadow IT apps. You’ll need a custom plan to start securing and optimizing your SaaS stack.
Bottom line
If your goal is to reduce risk, cut costs, and improve operational efficiency through a single pane of glass, it's a very strong choice.
4. Netskope
What it does: Netskope acts as a security proxy between users and cloud applications. It uses real-time traffic analysis to enforce granular data protection policies, like blocking uploads of client data to personal Dropbox.
Who it's for: Large enterprises where data security is non-negotiable and comprehensive protection justifies complexity.
Key features
- Real-time traffic analysis that identifies app usage in encrypted traffic.
- Granular policy enforcement, like blocking uploads to unauthorized AI tools.
- Data fingerprinting creates unique markers for sensitive files without complex regex rules.
- Context-aware policies that consider user, device, location, and activity.
Pros
- Real-time threat protection blocks malware from cloud storage sync clients.
- Granular policies for precise control over data movement.
- Integration with existing security infrastructure.
Cons
- Deployment may require dedicated security team resources.
- Some users report network performance impacts.
- Licensing is expensive for small teams.
Pricing overview
Custom pricing that typically requires a significant budget allocation.
Bottom line
It is a good option when your priority is not just knowing about shadow IT, but actively controlling what data can be accessed and shared within it.
5. Torii

What it does: Torii uses AI-powered discovery to discover SaaS, AI, and desktop tools. It provides workflow automation to manage the entire SaaS lifecycle from procurement to offboarding.
Who it's for: IT teams overwhelmed by manual SaaS management who want to automate shadow IT workflows rather than just generate reports.
Key features
- No-code workflow builder automates employee onboarding and offboarding across discovered applications.
- Rich security context provides breach history, compliance status, and risk ratings for each discovered app.
- Real-time view of licensing, spend, and owner.
Pros
- Cross-functional dashboards designed for IT, finance, and security team collaboration
- It centralizes access removal and license cleanup.
- It’s easy to set up.
Cons
- Limited integrations (just 150) mean fewer data points for detailed insights into all applications.
- It doesn’t evaluate risk scores or threat levels.
- Reporting features need improvement, like adding a data slicing option.
Pricing overview
It has a Professional plan for managing the SaaS lifecycle and an enterprise tier that comes with custom integrations and cost optimization features. Plans are custom.
Bottom line
Most user reviews mention that it helped them improve onboarding and offboarding, but you can also use it to surface shadow IT apps.
6. ManageEngine SaaS Manager Plus

What it does: ManageEngine SaaS Manager Plus provides automated SaaS discovery through SSO integration and expense analysis. It has built-in license management, renewal tracking, and centralized compliance documentation designed for the ManageEngine IT suite.
Who it's for: Organizations already invested in the ManageEngine ecosystem who want shadow IT detection without switching platforms.
Key features
- Automated continuous scanning for active SaaS applications.
- OCR invoice processing automatically extracts contract details from uploaded documents.
- Centralized vendor management tracks contracts, renewal dates, and payment terms.
- Compliance document management for every app.
Pros
- Easy integration with ServiceDesk for ticketing and workflow management.
- License management and renewal tracking capabilities.
- Cost-effective add-on pricing for organizations already in the ecosystem.
Cons
- It doesn’t discover shadow AI, just SaaS apps.
- It lacks automated onboarding or offboarding features that most tools in this list have.
Pricing overview
Subscription-based model that starts at $250 for up to 5 apps and $7500 for up to 200 apps, billed yearly. You can manage up to 2 apps after your 30-day free trial.
Bottom line
Solid choice if you already use the ManageEngine service desk.
7. Zylo
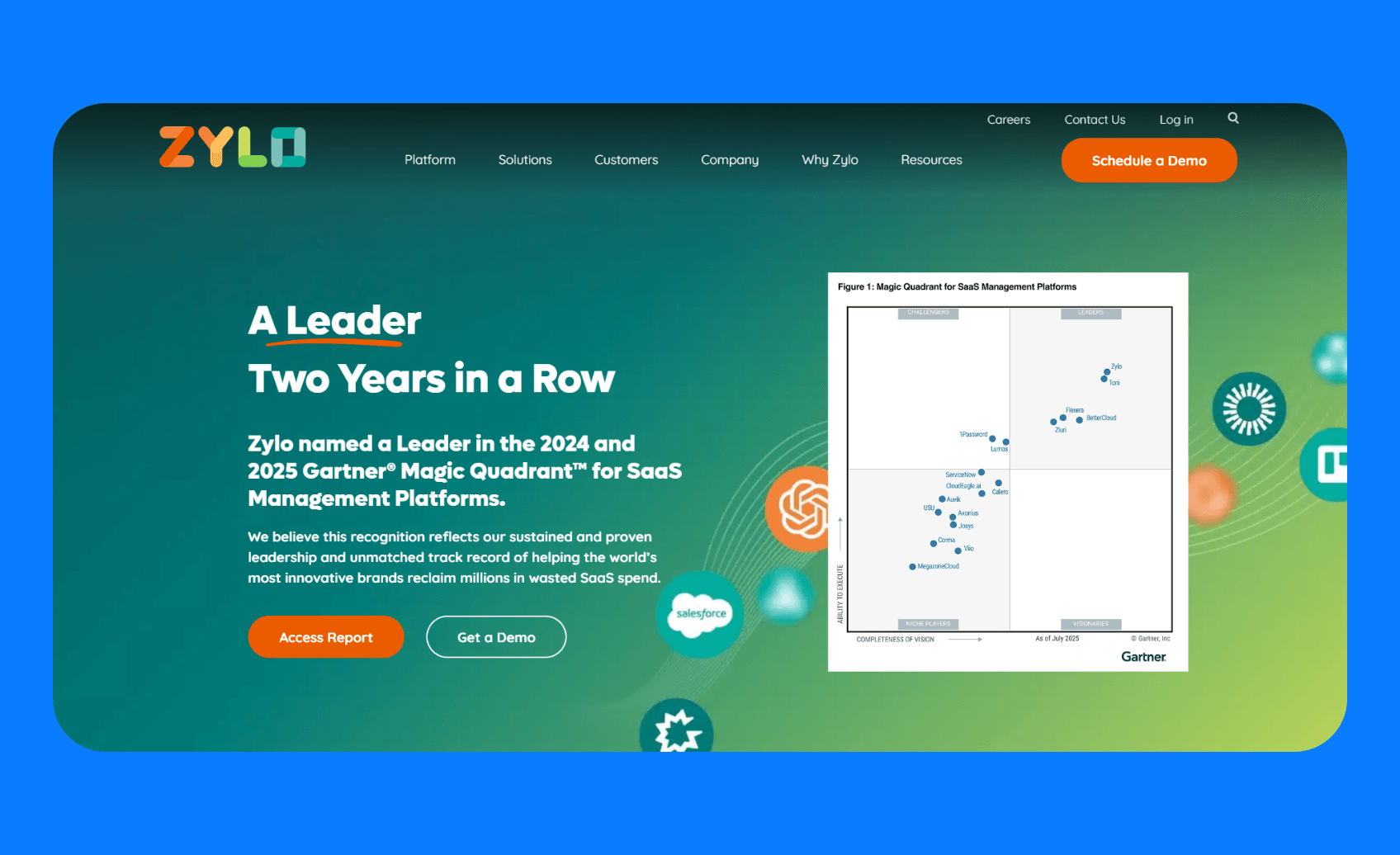
What it does: Zylo uses an AI-powered Discovery Engine that analyzes financial transactions, expense reports, and usage data to identify SaaS applications in your organization.
Who it's for: Enterprise IT leaders who need discovery capabilities and organizations struggling with shadow AI adoption, where traditional detection methods fail to identify AI tools purchased through personal expenses.
Key features
- AI-powered discovery engine uses machine learning to identify both known and unknown SaaS apps.
- Verified usage tracking showing actual time spent, not just logins.
- Shadow AI detection specifically identifies AI tools like ChatGPT, Claude, and other AI-native applications.
- Real-time spend tracking across all departments with automated alerts for new purchases.
Pros
- It has specific policies for AI tool detection and management.
- Renewal management prevents surprise auto-renewals with proactive contract tracking.
- It has native integrations for the SaaS you use, plus an API for your custom internal systems.
Cons
- Heavy reliance on Okta for usage tracking means apps not behind SSO are harder to monitor.
- Initial setup requires significant manual data scrubbing to ensure information accuracy.
Pricing overview
Pricing is custom.
Bottom line
When you need to find both shadow AI and IT apps your employees are expensing, use it.
How to choose the right shadow IT management stack
Start with your biggest pain point, choose a tool that solves it well, and then build out your stack over time as your needs and resources grow.
When comparing tools, look for:
- App discovery across all sources
- Breadth of SaaS integrations and custom API options
- Built-in vendor compliance checks
- Automated workflows for granting or revoking access
Here’s a decision framework for the tools we’ve covered:
- If you don’t know what’s in use, start with Zluri or Zylo to build an app inventory.
- If data leakage is your main concern, go for a security-first tool like Netskope that can sit in the middle of your traffic and enforce policy.
- If your main driver is to cut costs, you need a tool like ManageEngine that also discovers duplicate subscriptions and unused licenses.
Once you’ve mapped your SaaS, automate onboarding, license management, and policy enforcement.
Then, when you’re no longer just reacting, think about proactively preventing shadow apps. Superblocks can help with that. It provides a governed development environment with unified visibility for your employees to build the tools they need.
In most cases, you’ll mix and match. For example, use Zluri to discover SaaS apps, then Superblocks to consolidate your tooling on a secure platform.
How to eliminate shadow IT
Use a governance framework that gives teams freedom but also gives IT visibility.
Here’s a simple five-step approach:
- Discover apps and data flows: You can’t govern what you can’t see. Start by mapping all SaaS apps, browser extensions, and connected tools in use across teams.
- Assess risk and classify apps: Once you have visibility, sort each tool by risk level. It will help you decide which apps to approve, sandbox, or retire.
- Automate approvals and access: Build automated workflows that handle access requests, license provisioning, and revocations. Some detection tools come with these features.
- Apply policy via Superblocks or similar: Once you’ve stabilized discovery and access, reduce the need for shadow apps entirely. Platforms like Superblocks give employees a governed, secure space to build or automate what they need without leaving IT in the dark.
- Monitor and educate employees: Continuously track usage patterns, flag new tools, and keep people informed about data handling risks. A culture of transparency is the best long-term defense against shadow systems.
The future of shadow IT and AI governance
Most SaaS vendors are adding AI features to their platforms. As a result, shadow AI usage increasingly occurs inside approved tools, not just in unapproved apps.
You'll need visibility into apps and the models or APIs they're calling behind the scenes.
The old approach of blocking everything isn’t realistic anymore. AI saves your teams hours every day. There’s no putting that genie back in the bottle.
The smarter move is to build safe, governed AI environments where employees can experiment within clear boundaries.
And as regulations like the EU AI Act and new AI policies in other countries like the US, Canada, and Singapore are piloted or proposed, your AI governance frameworks will need to evolve with compliance requirements.
Use Superblocks to manage shadow IT and AI
Superblocks works as both a prevention and remediation platform. Instead of turning to unapproved tools, teams can quickly build the apps they need fast and securely within the platform.
Also, when you uncover a shadow app, Superblocks provides the ideal off-ramp. You can recreate the app’s essential functionality and not disrupt workflows.
We’ve looked at the key features that enable this, but just to recap:
- Flexible development modalities: Teams can use Clark to generate apps from natural language prompts, then refine them in the WYSIWYG drag-and-drop visual editor or in code. Changes you make in code and the visual editor stay in sync.
- Context-aware AI app generation: Every app built with Clark automatically abides by organizational standards for data security, permissions, and compliance. This addresses the major LLM risks of ungoverned shadow AI apps.
- Centrally managed governance layer: It supports granular access controls with RBAC, SSO, and audit logs, all centrally governed from a single pane of glass across all users. It also integrates with secret managers for safe credentials management.
- Keep data on prem: It has an on-prem agent you can deploy within your VPC to keep sensitive data in-network.
- Extensive integrations: It can integrate with any API or databases. These integrations include your SDLC processes, like Git workflows and CI/CD pipelines.
- Forward-deployed engineering support: Superblocks offers a dedicated team of engineers who’ll guide you through implementation. This speeds up time to first value and reduces workload for your internal platform team.
If you’d like to see Superblocks in action, book a demo with one of our product experts.
Frequently asked questions
How is shadow AI different from shadow IT?
Shadow AI refers to employees or teams using AI tools like ChatGPT, Copilot, or Midjourney without IT oversight, while shadow IT covers any unsanctioned software, apps, or devices used outside approved systems.
Does Superblocks discover Shadow IT?
Superblocks doesn’t discover Shadow IT, but it prevents it by governing how teams build and use AI and internal tools.
Why do enterprises need both discovery and management tools?
Enterprises need both discovery and management tools because discovery identifies what’s in use, while management helps teams enforce policies and limit access.
How should Shadow IT and Shadow AI be managed together?
Shadow IT and shadow AI should be managed together through a unified governance framework that covers visibility, access control, and policy enforcement. Use discovery tools to map usage, enforce access controls across SaaS and AI layers, and give teams safe spaces like Superblocks to build and automate within policy.
Does low-code prevent shadow IT?
Low-code can prevent shadow IT by giving teams approved ways to build, but it can also become shadow IT when teams use personal accounts to solve their problems.
Stay tuned for updates
Get the latest Superblocks news and internal tooling market insights.
Request early access
Step 1 of 2
Request early access
Step 2 of 2
You’ve been added to the waitlist!
Book a demo to skip the waitlist
Thank you for your interest!
A member of our team will be in touch soon to schedule a demo.
Table of Contents



.png)
.png)
%20(1).png)